Digital Device Security at the School of Medicine
The School of Medicine is dedicated to encrypting all Stanford-owned computers used by Stanford employees who work at the school, and to encrypting all Stanford-owned or personally-owned computers and mobile devices used by Stanford employees and affiliates who work with High Risk Data (previously Restricted or Prohibited Data). (As of May 31, 2015, all computers on the Stanford network should be encrypted as well.)
FAQ General FAQs
The Stanford University Data Security Policy requires all School of Medicine employees (includes faculty, staff, postdocs, residents, and students to complete an attestation to declare their access to High Risk (previously Restricted or Prohibited) data, including PHI, and to inventory their computers and mobile devices that are used for Stanford business.
The Data Security policy requires verifiable encryption for all laptops and desktops.
Devices used by individuals who attest to using or accessing High Risk data must use the encryption tool SWDE (Stanford Whole Disk Encryption), which includes installation of BigFix to provide acceptable encryption verification. This includes Stanford-owned and personally-owned computers as well as VM machines used for Stanford business.
The policy also requires individuals to enroll all mobile devices used for Stanford work in Mobile Device Management (MDM), to enable encryption and strong password protection. Given the particular risk and frequency of loss or theft of smartphones and tablets, and the requirement to investigate each loss when the device is not encrypted, the School of Medicine requires that MDM be installed on all Stanford-owned and personally-owned devices for which we have an MDM solution. MDM also provides provides the ability to remotely erase a device if it is lost or stolen. Devices which cannot be enrolled in MDM must not be used by individuals who may access High Risk data.
Compliance with the policy requires the following actions:
All SoM Community Members
1. Everyone at the medical school will be asked to complete a Data & Device Attestation to identify whether you are exposed to High Risk data, and to identify the devices you use. Please only report the Stanford-owned and personally-owned devices that you use for Stanford business. You do not need to report devices owned by SHC or SCH.
2. Any iOS and Android (OS 4.0+) device may be enrolled in the Mobile Device Management program. All mobile devices used by individuals with access to High Risk Data must be enrolled in Stanford's Mobile Device Management program. See: MDM Installation guide »
All SoM devices must have a Restricted MDM profile, and not a Basic profile, regardless of whether you work with restricted data. If you currently have a Basic profile set up for a device, the only way to get a Restricted profile is to unenroll and re-enroll the device.
3. All Stanford-owned and personally-owned computers and VM machines on the Stanford network must be encrypted. Individuals who may store or access High Risk data must specifically use SWDE (Stanford Whole Disk Encryption); other users may use VLRE instead if they wish. SWDE includes BigFix, which is required to meet encryption verification requirements. See: BigFix Installation guide »
4. Everyone using BigFix must complete a Device Identification Survey to identify the use of each computer for Stanford business. This survey will be delivered to you via a BigFix pop-up screen on each of your computers.
Stanford employees who work at the School of Medicine
5. All networked computers and laptops used by Stanford employees for school business must be encrypted using Stanford's sanctioned whole disk encryption. Users who may access High Risk data must use SWDE for encryption. Users who will never access High Risk data can use a separate whole disk encryption tool developed by University IT called VLRE.
People who work with High Risk Data
6. All laptops and desktops (whether Stanford or personally owned) that may be used to interact with High Risk data (previously Restricted or Prohibited data) must be encrypted with the SWDE application. This includes all computers used to access the EPIC system used by both the adult and children's hospitals. For most individuals at the School, these services will be deployed automatically to your computer via the BigFix management tool. See: Installation FAQs »
To support the encryption of devices, the School provides various options for getting help. You can make use of the self-service materials on this site, your local IT support personnel, 650-725-8000, or visit us at our drop-in location in the Alway Building, room M108. See: Drop-in Location »
Data security is a critical priority for the School of Medicine and Stanford University at large. Stanford University policy states that all computers and devices used for Stanford business by University employees must be encrypted. This includes both Stanford-owned and personally-owned machines.
Encryption provides security for your patient or other important data should your device be lost or stolen because the data cannot be accessed without the decryption password. Any machine that is used regularly for Stanford work has a high likelihood of storing Stanford's High Risk data, either now or in the future, and the potential consequences are very severe should that data ever be compromised. It is very common for an individual computer user to not be fully aware of all the data that is stored, even temporarily, on their devices but that can be discovered upon investigation. This policy was developed to protect patients, the Institution and individual faculty, students and staff.
Stanford University data security policy states that anyone who attests to working with High Risk Data (including PHI) must bring all computers and mobile devices used for Stanford work, whether Stanford-owned or personally-owned, into full compliance with the University's data security policy.
Even though is it is possible to access EPIC and other tools through secure portals, any machine that is used regularly for Stanford work has a high likelihood of storing Stanford's High Risk data, either now or in the future, and the potential consequences are very severe should that data ever be compromised. It is very common for an individual computer user to not be fully aware of all the data that is stored, even temporarily, on their devices but that can be discovered upon investigation. This policy was developed to protect patients, the Institution and individual faculty, students and staff.
You can amend your response to the Data & Device Attestation simply by going back to the survey link and resubmitting your answers; your original response will be overwritten. Go to: Data & Device Attestation Survey
Please only report the Stanford-owned and personally-owned devices that you use for Stanford business. You do not need to attest for devices owned by SHC or LPCH.
Note: this attestation is different from the Device Identification Survey, which will appear as a popup on each of your computers that have BIgFix installed.
The Device Identification survey for a computer can be accessed through the BigFix dashboard on that computer.
1. To access the dashboard, click on the BigFix icon.

On Windows, the icon will appear in
the Windows task tray.

On Mac, the icon will appear in the top nav bar.
2. To access the Device Identification survey, click on the Offers tab in BigFix dashboard. Then click on the option that reads: I want to change the information I registered for this machine; this will open up a detailed description of this offer.
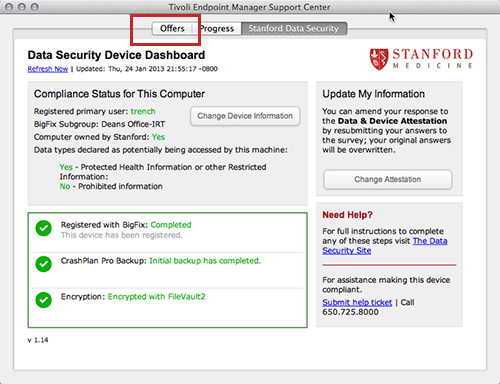
3. Accept the offer by clicking on the link that appears at the end of the offer description. A Big Fix popup window offering this survey should appear shortly. There are some cases where the window may be delayed.

Federal law requires strict security precautions for certain kinds of information, to protect against unauthorized access. Stanford cagegorizes this legally-protected information as High Risk Data. Examples include Protected Health Information (PHI), Social Security Numbers, and financial account numbers. The goal of the SoM Data Security Program is to ensure all faculty, staff, students, postdocs, residents, fellows and other Stanford affiliates at the school follow the required security precautions. For more information about High Risk data and Stanford policy, see http://dataclass.stanford.edu/
The School of Medicine has created a tool called AMIE ("Am I Encrypted?") which allows you to understand your compliance with the School of Medicine data security policies. The tool displays the information you supplied in your attestation and the BigFix, backup and encryption status of each of your computers. It also provides instructions to take actions to correct any issues that are detected. Please note that for a computer to report its status correctly, BigFix must be functioning properly and you will need to have completed the Device Identification Survey, which will appear as a BigFix popup on that machine. Please visit this site to see your current status: https://med.stanford.edu/datasecurity/amie/

As of May 2015, a new set of classifications has been established and is now in effect for Stanford data: High Risk, Moderate Risk, and Low Risk. The former framework - Prohibited, Restricted, Confidential, and Unrestricted - will be phased out by January 2016.
Information is classified as High Risk if protection of the information is required by law/regulation or Stanford is required to self-report to the government and/or provide notice to the individual if information is inappropriately accessed. Examples include:
- Social Security Numbers
- Credit Card Numbers
- Financial Account Numbers, such as checking or investment account numbers
- Driver's License Numbers
- Health Insurance Policy ID Numbers
- Health Information, including Protected Health Information (PHI)
- Passport and visa numbers
- Export controlled information under U.S. laws
As of May 2015, a new set of classifications has been established and is now in effect for Stanford data: High Risk, Moderate Risk, and Low Risk. The former framework - Prohibited, Restricted, Confidential, and Unrestricted - will be phased out by January 2016.
As of May 31, 2015, all computers used on the Stanford network must be encrypted, whether they are Stanford-owned or personally-owned. If a person declares that they use or access High Risk data in their role at Stanford, all computers they use for Stanford work must be encrypted specifically with SWDE, and they must fully comply with all aspects of the policy.
If you use a Stanford-owned or personally-owned device to access the hospitals' EPIC systems, it is subject to the school's Data Security policy and must be encrypted with school-mandated services.
If you don't regularly work with High Risk data but think you may occasionally be exposed to it through email or occasional files, err on the side of caution and encrypt your device with SWDE.
For more information on High Risk Data, please visit Stanford's Data Classification website.
If you are a Stanford employee, you will need to use a University-approved encryption method on any device used for School business.
If you are a Stanford affiliate who works with High Risk data, you will need to use the SWDE encryption process for every personally-owned device that might store or access Stanford's High Risk data (including electronic PHI or ePHI). This includes any device used to access the hospitals' EPIC systems.
If you are a Stanford employee who may interact with High Risk data, and use your personal computer for School business, you must use Stanford's SWDE encryption process. If you don't use your computer for High Risk data but you use it on the Stanford network on campus, you must encrypt it, using either SWDE or VLRE.
If you have declared that you use or access High Risk Data in your role at Stanford, all computers you use for Stanford work, including personally-owned machines, must be SWDE-encrypted and must fully comply with all aspects of the policy.
If you use a Stanford- or personally-owned device to access the hospitals' EPIC systems, it is subject to the University's Data Security policy and must be encrypted using the SWDE tool.
If you don't regularly work with High Risk data but you may occasionally be exposed to it through email or occasional files, you should encrypt your devices with SWDE.
For more information on High Risk data, please visit Stanford's Data Classification website.
Any employee who has lost, or had stolen, a device used for Stanford business is responsible for following all school procedures. This includes reporting the situation immediately to the Stanford University Privacy Office. See reporting procedure »
Yes. The Data Security policy mandates that all computers used for Stanford High Risk data, including VM machines, run the BigFix management software.
If the host machine is used by Stanford employees, it must be encrypted.
If the host machine is used to work with High Risk data, it (the host computer, not the VM) must have Stanford's Whole Disk Encryption software (SWDE) installed, and any associated VM machine will by definition be compliant.
If you work with PHI or other High Risk data, any computer that you use regularly does need to be encrypted. You should avoid using family members' computers since it is possible you may inadvertently place PHI on the device, which could be problematic if that device goes missing or is compromised.
We have seen many cases where this has happened without the person using the computer knowing that it has happened, as in the case of opening attachments from Webmail. These are often stored on the host computer and can remain there, forgotten, for long periods of time. Personal computers can also be hacked and if they contain Stanford data could put the institution and you at risk.
We do certainly realize that it is sometimes necessary to check email or do other Stanford work from public computers. In general we recommend minimizing this to the degree that is reasonable and if you do, be careful not to open files or attachments from your email.
In recognition that the computing environment at the School of Medicine is complex, exceptions can be approved for devices that perform functions that might be impacted by encryption but are running specialized lab equipment, real-time research data collection and other specialized research applications. Exceptions must be applied for and must be appropriately secured based on recommendations from IRT's security team. To apply for an exception please see the Exceptions Request Form.


