As a result of recent changes to Stanford WebLogin, users of Stanford web applications protected with legacy WebAuth might need to go through two-step authentication twice.
If your WebAuth application requires two-step authentication, the user will need to log in and authenticate once with the new two-step screen, and then authenticate once with the legacy two-step screen. The legacy two-step authentication will go to the device that was the user’s default device before the March 30 change; the user cannot change this default on WebLogin.
What can users do to fix this?
Users will need to authenticate twice on legacy WebAuth sites that require two-step authentication. If necessary, however, they can take these steps to authenticate on their default device:
-
When asked to do two-step authentication on the new system, the user can click the Device drop-down menu to change their device.
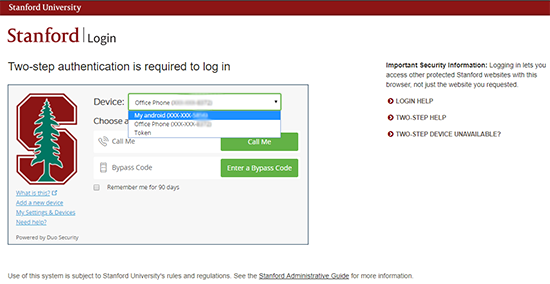
-
When asked to do two-step authentication on the legacy system, the user can click the Authenticate a different way link to choose their default device.
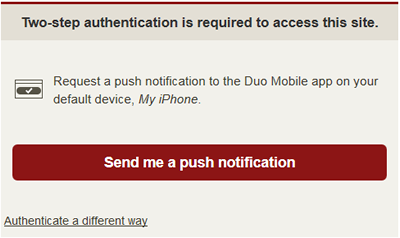
If it is difficult for the user to change their default device each time they do two-step authentication on a WebAuth site, they can submit a Help ticket to permanently update their default device on the WebLogin server.
How can application owners fix this?
To make logging in simpler for users, application owners can change their WebAuth sites so that they do not require two-step authentication every day. To disable requiring two-step authentication on your WebAuth site, look in your Apache configuration and remove any lines like
WebAuthRequireInitialFactor m
or
WebAuthRequireSessionFactor m
Owners can also resolve this problem by migrating their application to SAML 2.0, which you are strongly encouraged to do now. All owners of legacy WebAuth sites will be required to migrate to SAML 2.0 by August 31, 2018.
Why is this happening?
As of March 30, all legacy WebAuth sites now redirect users to the Stanford SAML IdP (Identity Provider) to authenticate, where the user logs in to Stanford Login and does a two-step authentication using the new Duo interface. The IdP then directs the user back to the WebLogin server.
The WebLogin server knows that the user logged in, but does not know whether or not the user did a two-step authentication. If the WebAuth application requires two-step authentication, it asks the user to do another two-step authentication on the legacy screen.
