Continuous Diagnostics and Mitigation (CDM)
Whether to provide important information, enable access to essential government services, or store sensitive information, information and communications technology is increasingly essential to fundamental government activities. While heightened connectivity has transformed and improved access to government, it has also increased the extent and complexity of our shared cybersecurity risk. Cyber attacks on federal government networks are growing more sophisticated, frequent, and dynamic. It is paramount that the government protects networks, systems, and information from unauthorized access or disruption while continually providing essential services to the public and protecting privacy, civil rights, and civil liberties.
The Continuous Diagnostics and Mitigation (CDM) program is a dynamic approach to fortifying the cybersecurity of government networks and systems. CDM provides federal departments and agencies with capabilities and tools that identify cybersecurity risks on an ongoing basis, prioritize these risks based upon potential impacts, and enable cybersecurity personnel to mitigate the most significant problems first. Congress established the CDM program to provide adequate, risk-based, and cost-effective cybersecurity and more efficiently allocate cybersecurity resources.
How CDM Works
The CDM program enables government entities to expand their continuous diagnostic capabilities by increasing their network sensor capacity, automating sensor collections, and prioritizing risk alerts.
CDM offers commercial off-the-shelf (COTS) tools, with robust terms for technical modernization as threats change. First, agency-installed sensors perform an automated search for known cyber flaws. Results feed into a local dashboard that produces customized reports, alerting network managers to their worst and most critical cyber risks based on standardized and weighted risk scores. Prioritized alerts enable agencies to efficiently allocate resources based on the severity of the risk. Progress reports track results, which can be used to compare security posture among department/agency networks. Summary information can feed into an enterprise-level dashboard to inform and situational awareness into cybersecurity risk posture across the federal government.
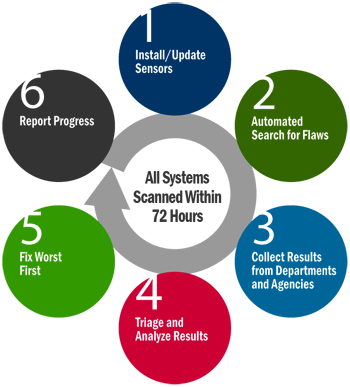
Benefits of CDM
DHS, in partnership with the General Services Administration, established a government-wide acquisition vehicle for continuous diagnostics and mitigation (CDM). The CDM blanket purchase agreement (BPA) is available to Federal, State, local, and tribal government entities. BPA participants achieve cost savings through tiered-price and task order discounts, enabling more efficient use of scarce resources to be spread further. This strategy results in an enterprise approach to continuous diagnostics, including consistent application of best practices.
The CDM Program enhances government network security through automated control testing and progress tracking. This approach:
- Provides services to implement sensors and dashboards;
- Delivers near-real time results;
- Prioritizes the worst problems within minutes, versus quarterly or annually;
- Enables defenders to identify and mitigate flaws at network speed; and
- Lowers operational risk and exploitation of government IT systems and networks.
Additionally, for federal cyber investments, the CDM program fulfills Federal Information Security Management Act (FISMA) mandates.
The CDM program is designed to rigorously ensure personal privacy. Data sent from CDM participant networks to DHS does not include any Personally Identifying Information (PII) or information about specific department or agency computers, applications or user accounts.
CDM Implementation
DHS and GSA are structuring acquisition vehicles on behalf of CDM participants. The CDM Blanket Purchase Agreement (BPA) is open to any government entity, including the Federal Civilian Executive Branch (.gov), as well as state, local, tribal, and territorial departments and agencies. For more information about the CDM contract award, visit www.gsa.gov/cdm.
For Federal Civilian Executive Branch departments and agencies, DHS:
- Optimizes CDM acquisitions;
- Organizes Task Order participants;
- Buys sensors and services with DHS-appropriated funds for .gov departments and agencies;
- Provides services to implement sensors and agency dashboards for .gov departments and agencies; and
- Provides federal dashboard-related infrastructure.
State, local, regional, and tribal governments may use the Direct Order/Direct Bill option to procure products and/or services from the CDM BPA via the delegated procurement authority, GSA Federal Systems Integration and Management Center (FEDSIM). For specific ordering options, please see GSA’s CDM/CMaaS Ordering Guide, 2013, via www.gsa.gov/cdm.
Based upon Congressional authorization and OMB guidance, DHS will work with departments and agencies to implement CDM in a consistent manner that demonstrates measurable cybersecurity results and leverages strategic sourcing to achieve cost savings. DHS will continue to actively collaborate with public sector partners every day to respond to and coordinate mitigation in the face of attempted disruptions to the Nation’s critical cyber and communications networks and to reduce adverse impacts on critical network systems.
The CDM Program covers 15 continuous diagnostic capabilities. The first phase of CDM focuses on endpoint integrity: management of hardware and software assets, configuration management, and vulnerability management, which are foundational capabilities to protect systems and data. Phases 2 and 3 are being further defined to include identity and infrastructure management.
CDM Phases
Phase 1:
- HWAM – Hardware Asset Management
- SWAM – Software Asset Management
- CSM – Configuration Settings Management
- VUL – Vulnerability Management
Phase 2: Least Privilege and Infrastructure Integrity
- TRUST –Access Control Management (Trust in People Granted Access)
- BEHV – Security-Related Behavior Management
- CRED – Credentials and Authentication Management
- PRIV – Privileges
Phase 3: Boundary Protection and Event Management for Managing the Security Lifecycle
- Plan for Events
- Respond to Events
- Generic Audit/Monitoring
- Document Requirements, Policy, etc.
- Quality Management
- Risk Management
- Boundary Protection (Network, Physical, Virtual)
 Official website of the Department of Homeland Security
Official website of the Department of Homeland Security
